 As part of a research, the Medical Device Security Center evaluated the security and privacy properties of a common ICD. They investigate whether a malicious party could create his or her own equipment capable of wirelessly communicating with this ICD. Wirelessly reprogrammable implantable medical devices (IMDs) such as pacemakers, implantable cardioverter defibrillators (ICDs), neurostimulators, and implantable drug pumps use embedded computers and radios to monitor chronic disorders and treat patients with automatic therapies. For instance, an ICD that senses a rapid heartbeat can administer an electrical shock to restore a normal heart rhythm, then report this event.
As part of a research, the Medical Device Security Center evaluated the security and privacy properties of a common ICD. They investigate whether a malicious party could create his or her own equipment capable of wirelessly communicating with this ICD. Wirelessly reprogrammable implantable medical devices (IMDs) such as pacemakers, implantable cardioverter defibrillators (ICDs), neurostimulators, and implantable drug pumps use embedded computers and radios to monitor chronic disorders and treat patients with automatic therapies. For instance, an ICD that senses a rapid heartbeat can administer an electrical shock to restore a normal heart rhythm, then report this event.
Given the anticipated evolution in IMD technologies, we believe that now is the right and critical time to focus on protecting the security and privacy of future implantable medical devices. IMDs pervasiveness continues to swell, with approximately twenty-five million U.S. citizens currently benefiting from therapeutic implants.
Pacemakers and ICDs are both designed to treat abnormal heart conditions. About the size of a pager, each device is connected to the heart via electrodes and continuously monitors the heart rhythm.
Pacemakers automatically deliver low energy signals to the heart to cause the heart to beat when the heart rate slows. Modern ICDs include pacemaker functions, but can also deliver high voltage therapy to the heart muscle to shock dangerously fast heart rhythms back to normal. Pacemakers and ICDs have saved innumerable lives, and there are millions of pacemaker and ICD patients in the U.S. today.
The Medical Device Security Center is a cross-disciplinary partnership between researchers at:
- the Beth Israel Deaconess Medical Center, Harvard Medical School,
- the University of Massachusetts Amherst, and
- the University of Washington.
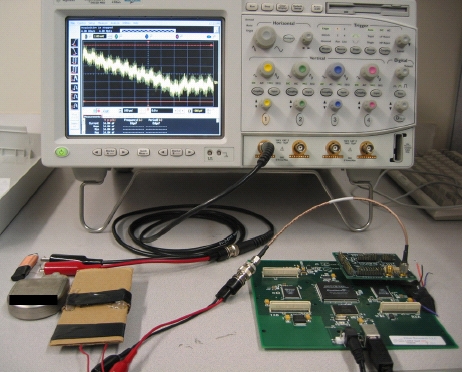 Using some equipment (an antenna, radio hardware, and a PC), they found that someone could violate the privacy of patient information and medical telemetry. The ICD wirelessly transmits patient information and telemetry without observable encryption. The adversary's computer could intercept wireless signals from the ICD and learn information including: the patient's name, the patient's medical history, the patient's date of birth, and so on.
Using some equipment (an antenna, radio hardware, and a PC), they found that someone could violate the privacy of patient information and medical telemetry. The ICD wirelessly transmits patient information and telemetry without observable encryption. The adversary's computer could intercept wireless signals from the ICD and learn information including: the patient's name, the patient's medical history, the patient's date of birth, and so on.
Using this same equipment (an antenna, radio hardware, and a PC), they also found that someone could also turn off or modify therapy settings stored on the ICD. Such a person could render the ICD incapable of responding to dangerous cardiac events. A malicious person could also make the ICD deliver a shock that could induce ventricular fibrillation, a potentially lethal arrhythmia.
Some IMDs, like pacemakers and ICDs, have non-replaceable batteries. When the batteries on these IMDs become low, the entire IMDs often need to be replaced. From a safety perspective, it is therefore critical to protect the battery life on these IMDs. Toward balancing security and privacy with safety and effectiveness, all three of our approaches use zero-power: they do not rely on the IMD's battery but rather harvest power from external radio frequency (RF) signals. They recommend the following zero-power approaches
- An audible alert to warn patients when an unauthorized party attempts to wirelessly communicate with their IMD.
- Implement cryptographic (secure) authentication schemes using RF power harvesting.
- A new method for communicating cryptographic keys ("sophisticated passwords") in a way that humans can physically detect (hear or feel). The latter approach allows the patient to seamlessly detect when a third party tries to communicate with their IMD.
Get more information here http://www.secure-medicine.org
| < Prev | Next > |
|---|







 In this section you'll find a list of companies and organizations working in the healthcare IT sector in Egypt.
In this section you'll find a list of companies and organizations working in the healthcare IT sector in Egypt.